Ever had the need to use PVLANs in conjunction with one or more trunks, but your Cisco-switch doesn’t support it? I did. And I found a solution. It works well, but if you need to trunk many PVLANs, then this is not the solution you’re looking for; get a 4500/6500 to play with instead.
I’ll be using my scenario as an example in this article, but you could use it for whatever other reasons you might have. At school we have a Cisco-lab, with 5 racks containing various Cisco-equipment. For a while now, there’s been situations where you’d really like a DHCP-server, TFTP-server, or similar, at hand. So, since we already had a VMware ESXi-server running in the lab, it was fairly easy to setup a dedicated lab-server. However, since this ESXi also had to be publicly available, and the lab-network shouldn’t be, we decided to use a trunk between the ESXi and our 3560G (sitting as a gateway between the lab, the servers, and the internet). Each VM is then assigned to their respective VLANs. All well so far.
If we now step a bit back, and look at the usage of the lab-network, there’s at least one problem with connecting all the 5 racks together on the same VLAN; since each rack often is used by different people, doing different kinds of labs – often at the same time, you could end up with lots of trouble (complaints about VLAN-mismatches, speed/duplex-mismatches, and since they often do the same labs, they’ll also use the same settings with VTP, OSPF, EIGRP, etc, which will probably lead to a lot of confusion). I’m not sure this is what PVLANs should be used for, but I thought this was an appropriate case.
If you’re not familiar with how PVLANs work, I’ll give you a short rundown as to how it works. Very simple explained, PVLANs is VLANS inside VLANS. You select a primary VLAN, and then you can split this VLAN into several types of PVLANs based on how you configure the ports. There are three types of ports;
- Promiscuous (?P?); This port-type is allowed to send and receive from any other port-type that resides on the same primary VLAN.
- Isolated (?I?); This port-type is only allowed to communicate to ?P?-ports. They cannot communicate with other ?I?-ports, even if they have the same primary VLAN.
- Community (?C?); This port-type is allowed to communicate with ?P?-ports, and with ?C?-ports within the same secondary VLAN. They cannot communicate with ?I?-ports.
Now you probably wonder what I mean with primary- and secondary VLANs. The primary VLAN is the VLAN that ?P?-ports will use to send frames downstream to ?I?- and ?C?-ports. The secondary VLANs is what the ?I?- and ?C?-ports will use to send frames upstream to the ?P?-ports. So, in total, there are three types of VLANs we’ll use when we’re dealing with PVLANs;
- Primary VLAN; Used when the ?P?-ports is sending frames downstream to ?I?- and ?C?-ports.
- Secondary Isolated VLAN; Used when ?I?-ports forward frames to the ?P?-ports. Since all ?I?-ports is isolated from each other, we only need to use one isolated VLAN to connect all ?I?-ports to the ?P?-ports.
- Secondary Community VLANs; Used to transport frames between ?C?-ports with the same group/community-VLAN, and to transport frames upstream to the ?P?-ports.
So, now that we have a brief overview of how PVLANs works, we’ll get started with the actual configuring. I’ll show you my superb Visio-skills in the following illustration;
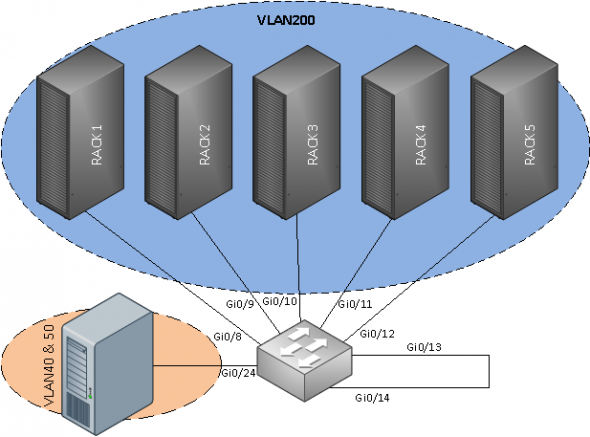
So, to configure the ports for the five racks, we’ll first create the necessary VLANs;
Switch(config)#vlan 200 Switch(config-vlan)#name PVLAN-RACKS Switch(config-vlan)#private-vlan isolated Switch(config-vlan)#vlan 210 Switch(config-vlan)#name PVLAN-PROMISC Switch(config-vlan)#private-vlan primary Switch(config-vlan)#private-vlan association 200
And then we’ll add the associations to the different switchports;
Switch(config)#interface GigabitEthernet0/8 Switch(config-if)#description RACK1 Switch(config-if)#switchport access vlan 200 Switch(config-if)#switchport private-vlan host-association 210 200 Switch(config-if)#switchport mode private-vlan host Switch(config-if)#spanning-tree portfast Switch(config-if)#interface GigabitEthernet0/9 Switch(config-if)#description RACK2 Switch(config-if)#switchport access vlan 200 Switch(config-if)#switchport private-vlan host-association 210 200 Switch(config-if)#switchport mode private-vlan host Switch(config-if)#spanning-tree portfast Switch(config-if)#interface GigabitEthernet0/10 Switch(config-if)#description RACK3 Switch(config-if)#switchport access vlan 200 Switch(config-if)#switchport private-vlan host-association 210 200 Switch(config-if)#switchport mode private-vlan host Switch(config-if)#spanning-tree portfast Switch(config-if)#interface GigabitEthernet0/11 Switch(config-if)#description RACK4 Switch(config-if)#switchport access vlan 200 Switch(config-if)#switchport private-vlan host-association 210 200 Switch(config-if)#switchport mode private-vlan host Switch(config-if)#spanning-tree portfast Switch(config-if)#interface GigabitEthernet0/12 Switch(config-if)#description RACK5 Switch(config-if)#switchport access vlan 200 Switch(config-if)#switchport private-vlan host-association 210 200 Switch(config-if)#switchport mode private-vlan host Switch(config-if)#spanning-tree portfast
Next up comes the ?tricky? part. I’ll first show you the configuration for the trunk between our switch, and the ESXi-server;
Switch(config)#interface GigabitEthernet0/24 Switch(config-if)#description ESXi Switch(config-if)#switchport trunk encapsulation dot1q Switch(config-if)#switchport trunk native vlan 100 Switch(config-if)#switchport trunk allowed vlan 40,50 Switch(config-if)#switchport mode trunk
As you can see, just a normal trunk-setup. The actual ?hack?, is to ?enable? VLAN 50 on Gi0/24 as a promiscuous port. Since we’re not using a 4500/6500, this cannot be done by just typing a command in CLI. The way I solved this, was to make Gi0/14 an access-port to VLAN 50, and then connect Gi0/14 to Gi0/13 with a normal, straight-through network-cable. I then made Gi0/13 the promiscuous port.
Switch(config)#interface GigabitEthernet0/13 Switch(config-if)#description PROMISC Switch(config-if)#switchport access vlan 100 Switch(config-if)#switchport private-vlan mapping 210 200 Switch(config-if)#switchport mode private-vlan promiscuous Switch(config-if)#no cdp enable Switch(config-if)#spanning-tree bpdufilter enable Switch(config-if)#interface GigabitEthernet0/14 Switch(config-if)#description VLAN50<->RACK Switch(config-if)#switchport access vlan 50 Switch(config-if)#switchport mode access Switch(config-if)#no cdp enable Switch(config-if)#spanning-tree bpdufilter enable
Thats all. This way we have full connectivity from the racks to the server, and back, but no traffic is allowed to pass from one rack to another.
“I?ll show you my superb Visio-skills in the following illustration;”
L O L!!
“Check out my new Visco-router…!”
http://office.microsoft.com/visio/
maybe we should add DHCP option 150 in the lab- dhcp..?
option 150 is tftp-server ;=)
Hi, I have ASA firewall. The Interface is trunk containing 2 vlans (vlan100 vlan 200). That interface is connected to 3750 switch. With the full findings available in Ole777 Chelsea